![[CVE-2025-6533] Captcha Replay](/_astro/image-20250613114237721.Drqh5NSG_WqYQF.webp)
[CVE-2025-6533] Captcha Replay
The login function fails to invalidate the captcha after one use. This allows an attacker to replay a valid captcha to bypass brute-force protection.
views
| comments
Abstract#
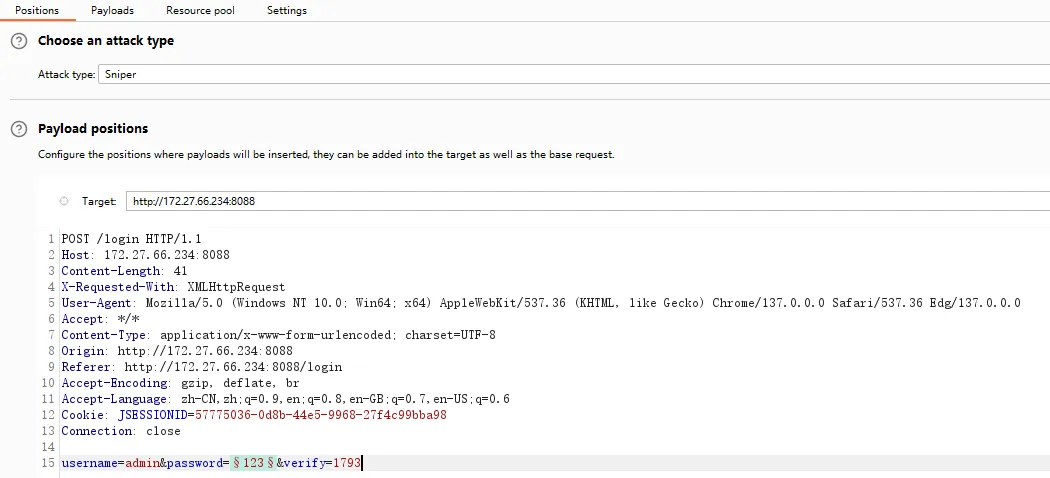
The ajaxLogin method in the authentication module is vulnerable to a Captcha Replay Attack. The application correctly validates the user-submitted captcha against the one stored in the session but fails to invalidate or remove the captcha after its first use. This allows an attacker to reuse a single valid captcha indefinitely to perform automated brute-force or dictionary attacks against user passwords, completely bypassing the anti-automation security control.
Vulnerability Details#
1. Affected Product Information
- Product Name: novel-plus
- Repository URL: https://github.com/201206030/novel-plus ↗
- Affected Component:
novel-admin/src/main/java/com/java2nb/system/controller/LoginController.java:80 - Affected Version:
v5.1.3 - Vulnerability Type: Improper Restriction of Excessive Authentication Attempts
- CWE (Common Weakness Enumeration): CWE-307
- Affected Code Snippet:
R ajaxLogin(String username, String password,String verify,HttpServletRequest request) {
try {
//从session中获取随机数
String random = (String) request.getSession().getAttribute(RandomValidateCodeUtil.RANDOMCODEKEY);
if (StringUtils.isBlank(verify)) {
return R.error("请输入验证码");
}
if (random.equals(verify)) {
} else {
return R.error("请输入正确的验证码");
}
} catch (Exception e) {
logger.error("验证码校验失败", e);
return R.error("验证码校验失败");
}
password = MD5Utils.encrypt(username, password);
UsernamePasswordToken token = new UsernamePasswordToken(username, password);
Subject subject = SecurityUtils.getSubject();
try {
subject.login(token);
return R.ok();
} catch (AuthenticationException e) {
return R.error("用户或密码错误");
}
}POC#